Anonymous: Tails OS with encrypted persistent disk space
📋 Overview
We’re going to create a Tails install that you can rely on for all of Tails OS’ anonymity features. Not only will we create a Tails device that contains Tails OS, but we’ll include an encrypted persistent partition that will give you disk space that is protected by a password.
Tails OS is amnesic; whatever you do on Tails OS will vanish as soon as you shutdown the computer and/or remove the Tails device. This is because everything you do within Tails OS is not written to the Tails device, but stored in your computers volatile memory. By default, Tails routes all traffic through the Tor network using onion routing to help you be anonymous. It is lauded by whistle blowers, journalists, hacktivists and other people who need anonymity.
Requirements:
- 8 GB+ USB flash drive, SD card (or R-DVD)
- A known-safe 64-bit x86-64 computer running Linux
- Note: Be sure to strip out the
$when copy/pasting any commands from below.
- Note: Be sure to strip out the
Before we dive into the work of both creating a Tails OS device, and adding a Veracrypt encrypted partition that supplies persistent disk space, lets better understand what Tails OS provides us. Below you’ll find info from the Tails OS website. If you don’t understand how Tails OS and the Tor network keeps you anonymous, its a great read… otherwise you can skip to the “Install Tails on USB stick or SD card” section.
💪 ALL about Tails OS
Tails is a portable operating system that protects against surveillance and censorship. It uses the Tor network to protect your privacy online and helps you avoid censorship. Tails leave no trace on your computer when shut down. It includes a selection of applications to work on sensitive documents and communicate securely - everything is ready-to-use and has safe defaults. Tails can be downloaded for free and independent security researchers verify their work. It’s based on Debian GNU/Linux.
To use Tails, you shut down your computer and start on your Tails USB stick instead of starting on Windows, MacOS or Linux. You can temporarily turn your own computer into a secure machine. You can also stay safe while using the computer of someone else. You don’t have to worry about the computer having viruses because Tails runs independently from the other operating system and never uses the hard disk. However, Tails cannot always protect you if you install it from a computer with viruses or if you use it on a computer with malicious hardware, like keyloggers.
Warning: Tails is safer than any regular operating system. But Tails, or any software or operating system, cannot protect you from everything - even if they pretend to:
Protecting your identity
-
Tails is designed to hide your identity, but some of your activities could reveal your identity:
- Sharing files with metadata, such as date, time, location and device information. To help you clean metadata, Tails includes Metadata Cleaner, a tool to remove metadata in a wide range of file formats.
- If you use Tails for more than one purpose at a time, an adversary could link your different activities together. For example, if you log into different accounts on the same website in a single Tails session, the website could determine that the accounts are used by the same person. This is because websites can tell when two accounts are using the same Tor circuit. To prevent this, restart Tails between activities.
Limitations of the Tor network
-
Tails uses the Tor network because it is the strongest and most popular network to protect from surveillance and censorship, but has limitations if you are concerned about hiding that you are using Tor/Tails or protecting your communications from attackers:
- Tails makes it clear that you are using Tor and probably Tails. Everything you do on Tails goes thru Tor. They protect you by making you look like any random user. Your ISP and local network can see that you connect to Tor, but cannot know what sites you visit. The sites you visit can know that you’re using Tor because the list of exit nodes is public. To hide that you’re connect to Tor you can use a Tor bridge.
- Exit nodes can intercept traffic to the destination server. Tor hides your location from server, but it doesn’t encrypt all your communication. The last relay of a Tor circuit, the exit node, establishes the actual connection to the destination server. The last step can be unencrypted:
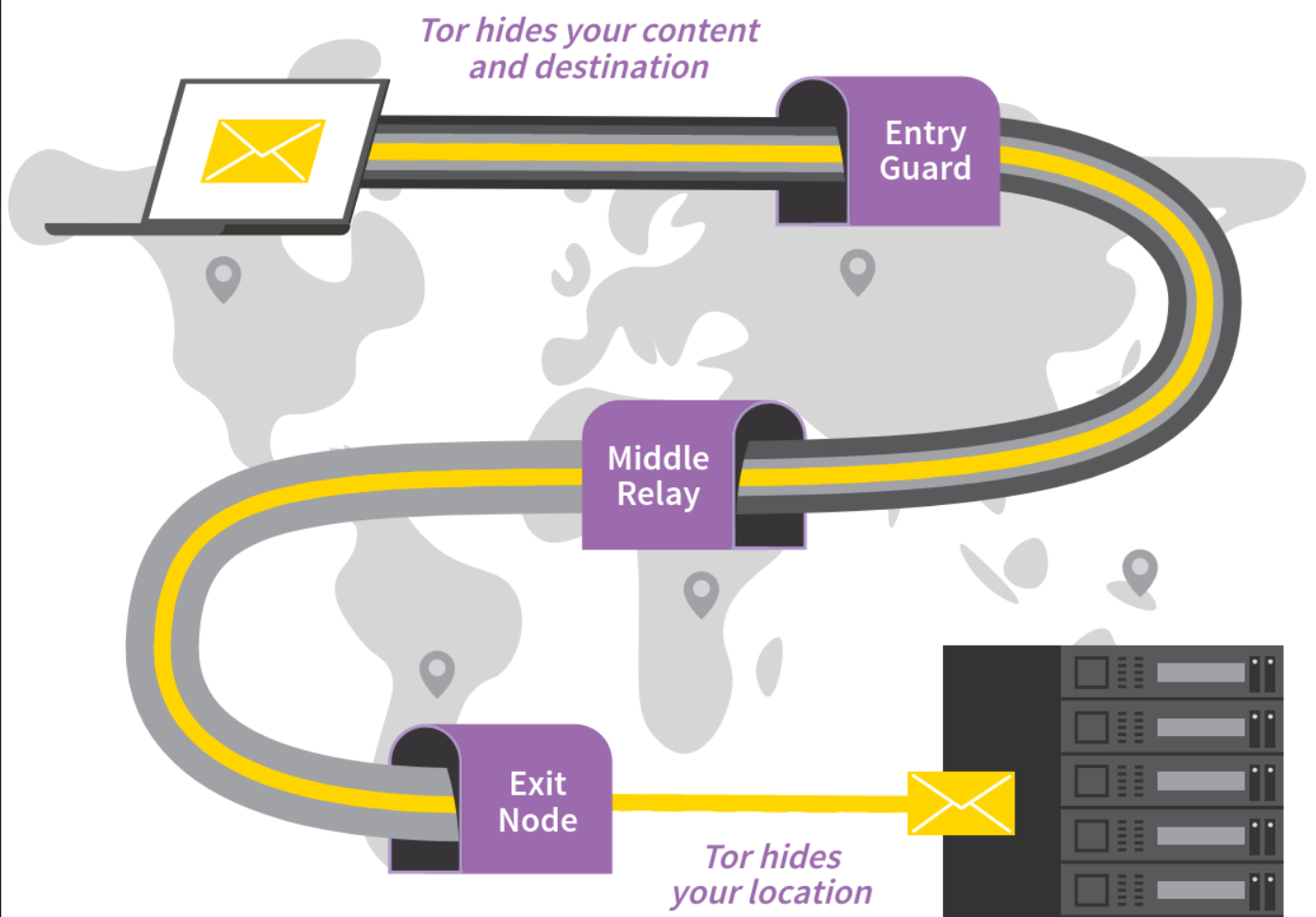
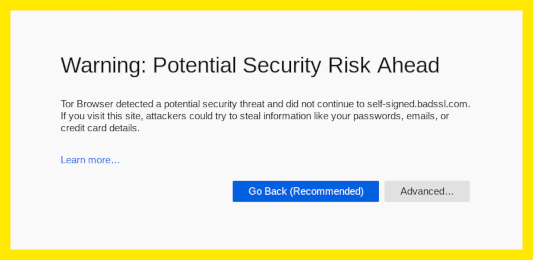
- The exit node can observe your traffic. Tails includes HTTPS Everywhere to encrypt the connection between the exit node and the destination server whenever possible. It can pretend to be the destination server, known as machine-in-the-middle attack (MitM), which is why you should pay attention to security warnings in Tor Browser. If you get such a warning, use the New Identity feature of Tor browser to change exit nodes:
- To learn more about what information is available to someone observing the different parts of a Tor circuit, see the interactive graphics at Tor FAQ: Can exit nodes eavesdrop on communications?.
- Adversaries watching both ends of a Tor circuit could identify users. An adversary, who could control the 3 relays in a circuit, could deanonymize Tor users. Tails takes extra measures to use different circuits for different applications. A powerful adversary, who could analyze the timing and shape of the traffic entering and exiting the Tor network, might be able to deanonymize Tor users. These attacks are called end-to-end correlation attacks, because the attacker has to observe both ends of a Tor circuit at the same time.
Reducing risks when using untrusted computers
- Install Tails from a computer you trust! Tails protects you from viruses and malware on your usual system because it runs independently from other operating systems, but your Tails might be corrupted if you install from a compromised operating system.
- Always install Tails from a trusted operating system - download Tails on a computer without viruses or clone Tails from a trusted Tails device.
- Do not plug your Tails device in while another operating system is running on the computer.
- Use your Tails device only to run Tails. Do not use your Tails device to transfer files to or from another operating system.
- If you worry that your Tails device might be corrupted, do a manual upgrade from a trusted operating system.
- No operating system can protect against hardware alterations. Your computer might be compromised if its physical components have been altered. For example, if a keylogger has been physically installed on your computer, all off your keystrokes could be stored and accessed by someone else, even though you’re using Tails.
- Try to keep your computer in a safe location or in your care at all times. Hardware alterations are more likely on public computers, in internet cafes or libraries and on desktop computers, where a device is easier to hide.
- If you worry that a computer might be modified:
- Use a password manager to paste saved passwords. This way, you don’t have to type passwords that might be visible to people or cameras near you.
- Use the Screen Keyboard, if you are using a public computer or worry that the computer might have a keylogger.
- Keyloggers are easy to buy and hide on desktop computers, but not on laptops.
- Other hardware alterations are much more complicated and expensive to install.
- No operating system can protect against BIOS and firmware attacks.
- Firmware includes the BIOS or UEFI and other software stored in electronic chips on the computer. All operating systems, including Tails, depend on firmware to start and run, so no operating system can protect against a firmware attack. In the same way that a car depends on the quality of the road it is driving on, operating systems depend on their firmware.
- Keeping your computer in a safe location can protect against some firmware attacks, but some other firmware attacks can be performed remotely.
Other Links
💾 Install Tails on USB stick or SD card . . .
Step 1: Download the Tails release
- Go to the Install Tails website and download the latest release for Linux.
- For further security, after downloading the release, scroll down to step 3/8 and verify the Tails .img file by clicking the
Select your download...button. You should see a response ofVerification successful! (tails-amd64-x.xx.img).- (Alternatively, you could download the OpenPGP signature and use gpg to verify the Tails .img] yourself, locally. You’ll first have to add the Tails signing key:
- For further security, after downloading the release, scroll down to step 3/8 and verify the Tails .img file by clicking the
$ curl https://tails.boum.org/tails-signing.key | gpg --import
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1346k 100 1346k 0 0 894k 0 0:00:01 0:00:01 --:--:-- 893k
gpg: key DBB802B258ACD84F: 2172 signatures not checked due to missing keys
gpg: key DBB802B258ACD84F: public key "Tails developers <tails@boum.org>" imported
gpg: Total number processed: 1
gpg: imported: 1
gpg: no ultimately trusted keys found
$ gpg --verify tails-amd64-5.13.img.sig
gpg: assuming signed data in 'tails-amd64-5.13.img'
gpg: Signature made Mon 15 May 2023 04:31:21 AM PDT
gpg: using RSA key 753F901377A309F2731FA33F7BFBD2B902EE13D0
gpg: Good signature from "Tails developers <tails@boum.org>" [unknown]
gpg: aka "Tails developers (offline long-term identity key) <tails@boum.org>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: A490 D0F4 D311 A415 3E2B B7CA DBB8 02B2 58AC D84F
Subkey fingerprint: 753F 9013 77A3 09F2 731F A33F 7BFB D2B9 02EE 13D0
Step 2: Burn tails to USB flash drive or SD card
I’m going to use the Linux command dd, but if you prefer a GUI application, balenaEtcher is a great choice.
Warning: One should be extremely cautious using dd, as it can destroy data irreversibly. It will erase any device you write to!
-
First, open a terminal and navigate to the directory where you downloaded the Tails OS .img.
-
Next, check your system by listing its block devices:
$ lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTS
nvme0n1 259:0 0 931.5G 0 disk
├─nvme0n1p1 259:1 0 512M 0 part /boot/efi
├─nvme0n1p2 259:2 0 1.7G 0 part /boot
└─nvme0n1p3 259:3 0 929.3G 0 part
└─nvme0n1p3_crypt 253:0 0 929.3G 0 crypt
├─vgubuntu-root 253:1 0 927.4G 0 lvm /
└─vgubuntu-swap_1 253:2 0 1.9G 0 lvm [SWAP]
- I have one device connected;
nvme0n1. Now, connect your USB flash drive and list again:
$ lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTS
sda 8:0 1 14.8G 0 disk
├─sda1 8:1 1 8G 0 part
└─sda2 8:2 1 6.8G 0 part
nvme0n1 259:0 0 931.5G 0 disk
├─nvme0n1p1 259:1 0 512M 0 part /boot/efi
├─nvme0n1p2 259:2 0 1.7G 0 part /boot
└─nvme0n1p3 259:3 0 929.3G 0 part
└─nvme0n1p3_crypt 253:0 0 929.3G 0 crypt
├─vgubuntu-root 253:1 0 927.4G 0 lvm /
└─vgubuntu-swap_1 253:2 0 1.9G 0 lvm [SWAP]
- You’ll now notice the
sdadevice. It’s my USB flash drive… it actually has data written to it; an Arch Linux install. This will be overwritten when we run theddcommand. Please be sure to correctly identify your USB flash drive and be aware that any data on it will be overwritten when we enter the following to write Tails to the device:
$ sudo dd if=tails-amd64-5.13.img of=/dev/sda
2590720+0 records in
2590720+0 records out
1326448640 bytes (1.3 GB, 1.2 GiB) copied, 94.2228 s, 14.1 MB/s
Once you see the records in/out output from the dd command, your Tails OS device is complete. You can remove it from the computer.
🔒 Add persistent storage and VeraCrypt!
Step 1: Booting into Tails OS for the first time
-
Insert your Tails OS flash drive into a computer and boot.
- Different computer brands have different buttons to press in order to select using a different boot drive. On ThinkPads you press the
ENTERkey. On frame.work laptops you press theF12key. Usually, a Google search for[BRAND NAME] boot device menuwill get you there… boot your computer and select your USB flash device as the boot medium.
- Different computer brands have different buttons to press in order to select using a different boot drive. On ThinkPads you press the
-
At the
Welcome to Tails!screen, click the+and set an Administrator Password. We will need this to create a partition for our encrypted persistent storage. After adding one, you can click theStart Tailsbutton!
You are now booted into Tails OS - but you don’t have a way to save data or install persistent packages. We’ll handle that now…
Step 2: Enabling persistence
-
Click
Applications,System Tools,Persistent Storage,Continueand set a passphrase. ClickCreate Persistent Storageand let Tails initialize LUKS and format the file system. -
Now, restart Tails OS. You’ll need to power off the Tails OS, wait for the computer to shutdown and then reboot, using the same key to select booting from the Tails OS device.
Step 3: Get VeraCrypt!!
-
At the
Welcome to Tails!screen, be sure to set an Administrator Password again, and this time unlock your Persistent Storage by adding the passphrase you set before and clickingUnlock Encryption. After is unlocks, you can clickStart Tails. -
You’ll need to connect to a network now; for Wi-Fi, click the
Wi-Fi Not Connectedbutton found in the user menu (Top right hand corner of the Tails OS menu bar), clickSelect Networkand enter your Wi-Fi password.- Once a network is established, you’ll notice a
Tor Connectionmenu pops up. SelectConnect to Tor automaticallyand click theConnect to Torbutton. (You’ll notice that you could configure a Tor bridge - this is the option you’ll use if you need to hide the use of Tor from an ISP or local network.)
- Once a network is established, you’ll notice a
-
After you see
Connected to Tor successfully, you can close theTor Connectionwindow. -
We’ll now import a VeraCrypt Team PGP key. Open a terminal and enter the command:
$ torsocks curl https://www.idrix.fr/VeraCrypt/VeraCrypt_PGP_public_key.asc | gpg --import
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 5434 100 5434 0 0 3257 0 0:00:01 0:00:01 --:--:-- 3255
gpg: key 0x821ACD02680D16DE: 1 signature not checked due to a missing key
gpg: key 0x821ACD02680D16DE: public key "VeraCrypt Team (2018 - Supersedes Key ID=0x54DDD393) <veracrypt@idrix.fr>" imported
gpg: Total number processed: 1
gpg: imported: 1
gpg: no ultimately trusted keys found
- We’re going to set an environment variable to subsequent commands work even if you’re reading this in the future and there’s newer VeraCrypt software. Grab the latest release number from that link; on 05/29/2023 it is
1.25.9. Use that number to set a variable using the command:
VC_RELEASE=1.25.9
-
Open the Tor Browser; click
ApplicationsthenTor Browserand download the latest release of VeraCrypt’s Linux Generic Installer using the same link that you just visited. Today the file is namedveracrypt-1.25.9-setup.tar.bz2, but it may change in the future… it will coincide with the number you set inVC_RELEASE=x.xx.x. You can save it to the suggested~/Tor Browserdirectory that Tor Browser suggests. While you’re here, also grab the PGP Signature that’s listed. Now now have two files in~/Tor Browser. -
Verify VeraCrypt with the command:
$ gpg --verify ~/Tor\ Browser/veracrypt-$VC_RELEASE-setup.tar.bz2.sig
gpg: assuming signed data in '/home/amnesia/Tor Browser/veracrypt-1.25.9-setup.tar.bz2'
gpg: Signature made Sun 20 Feb 2022 01:11:36 PM UTC
gpg: using RSA key 5069A233D55A0EEB174A5FC3821ACD02680D16DE
gpg: Good signature from "VeraCrypt Team (2018 - Supersedes Key ID=0x54DDD393) <veracrypt@idrix.fr>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 5069 A233 D55A 0EEB 174A 5FC3 821A CD02 680D 16DE
-
The
WARNING!is standard. -
Now we’ll extract and VeraCrypt and run the installer:
$ cd ~/Tor\ Browser/
$ tar xf veracrypt-$VC_RELEASE-setup.tar.bz2
$ ./veracrypt-$VC_RELEASE-setup-gui-x64
-
Type
2forExtract package file ... to /tmpand pressENTER. PressENTER, followed bySPACEBARuntil it prompts you to typeyesto accept the license terms. PressENTERtwice and you’ll be back at the terminal!- Note: We don’t have to delete the files in
~/Tor Browserbecause Tails OS is amnesic; files here are only saved to the computers memory!
- Note: We don’t have to delete the files in
-
We’ll create an
.AppImagewith the following commands:
$ cd ~/Persistent
$ tar xf /tmp/veracrypt_${VC_RELEASE}_amd64.tar.gz --strip-components 2 usr/bin/veracrypt
$ echo -n "./veracrypt" > veracrypt.AppImage
$ chmod +x veracrypt.AppImage
🧐 What now??
Well, you can now run the ~/Persistent/veracrypt.AppImage so long as you’ve unlocked your persistent storage when booting your Tails OS device (Or by clicking Places, Persistent and veracrypt.AppImage.)… doing so brings up the VeraCrypt software, where you can click Create Volume, then Create an encrypted file container and then choose between a Standard VeraCrypt volume or a Hidden VeraCrypt volume.
-
Standard
- A normal VeraCrypt volume.
-
Hidden
- It may happen that you are forced by someone to reveal the password to an encrypted volume. There are many situations where you cannot refuse to reveal the password (for example, due to extortion). Using a so-called hidden volume allows you to solve such situations without revealing the password to your volume.
- (There are two volumes in one encrypted file, with different passwords; one password gives access to the outer volume, and the other gives access to the inner one. An adversary won’t be able to know if there is an inner volume, giving you plausible deniability if in a… tough situation.)
- It may happen that you are forced by someone to reveal the password to an encrypted volume. There are many situations where you cannot refuse to reveal the password (for example, due to extortion). Using a so-called hidden volume allows you to solve such situations without revealing the password to your volume.
And you certainly have all the power and anonymity that Tails OS offers by itself. When you get to the desktop, be sure to connect to a Wi-Fi (and the Tor network) before you get going. There are ways have allow persistent features, like connecting to a Wi-Fi network - access these thru the Persistence Menu.
A cool feature that I’ll mention is that you can simply pull the USB stick at any time and Tails OS will remove all data from its memory immediately. This is very useful if you’re in a situation that you need to stop access to any data on the computer, but don’t have ample time.
I’d implore you to learn about the technologies we’ve discussed in this article - I’ll catch you next time!
-
Unleashing the Power of Tails OS: Your Ultimate Privacy Companion
-
VPN with Tails - The Basics You Need to Know
- Special thanks to Sun Knudsen - His Privacy Guides helped with a couple commands for installing the VeraCrypt GUI. I’ve come to trust his content and I think you can, too!!